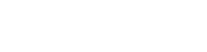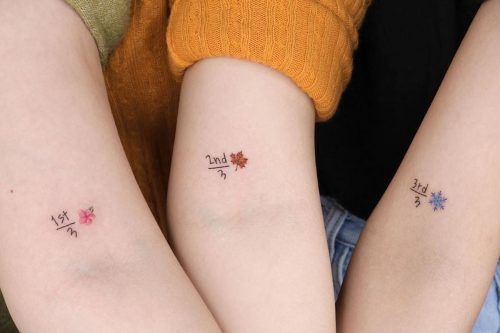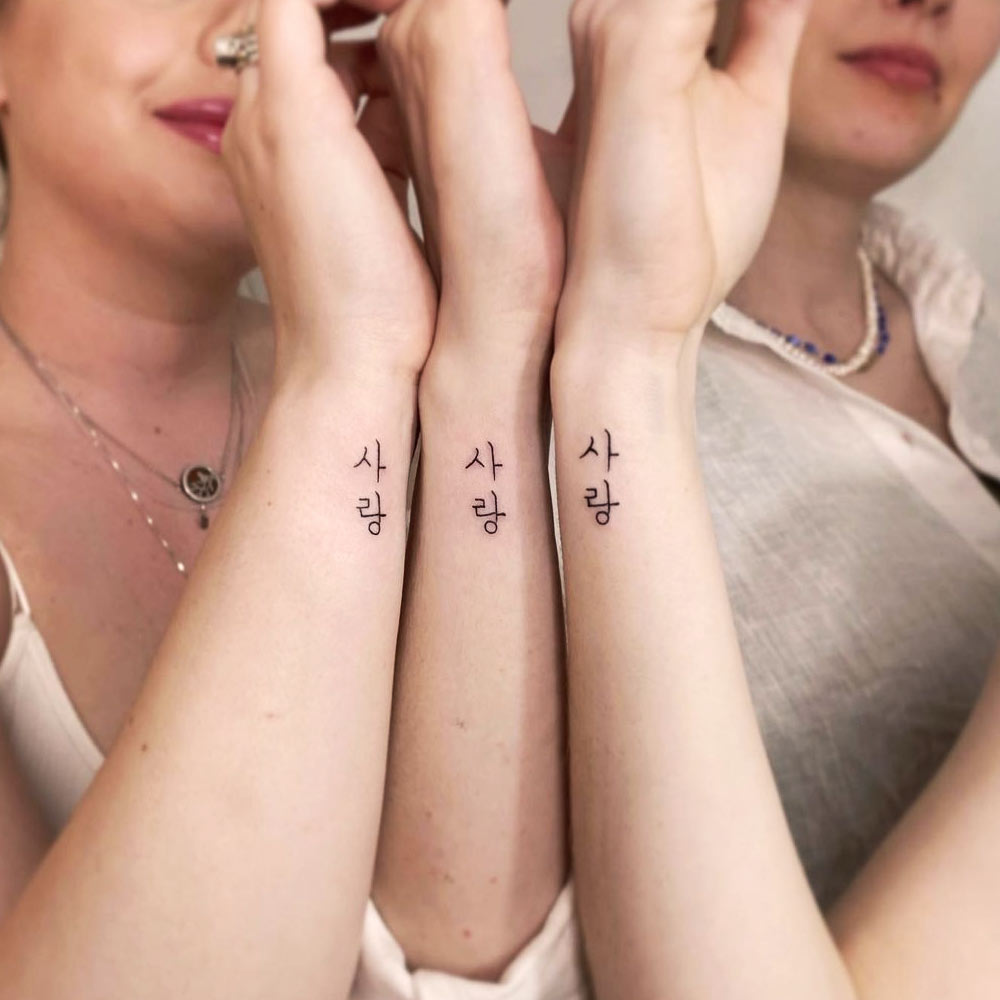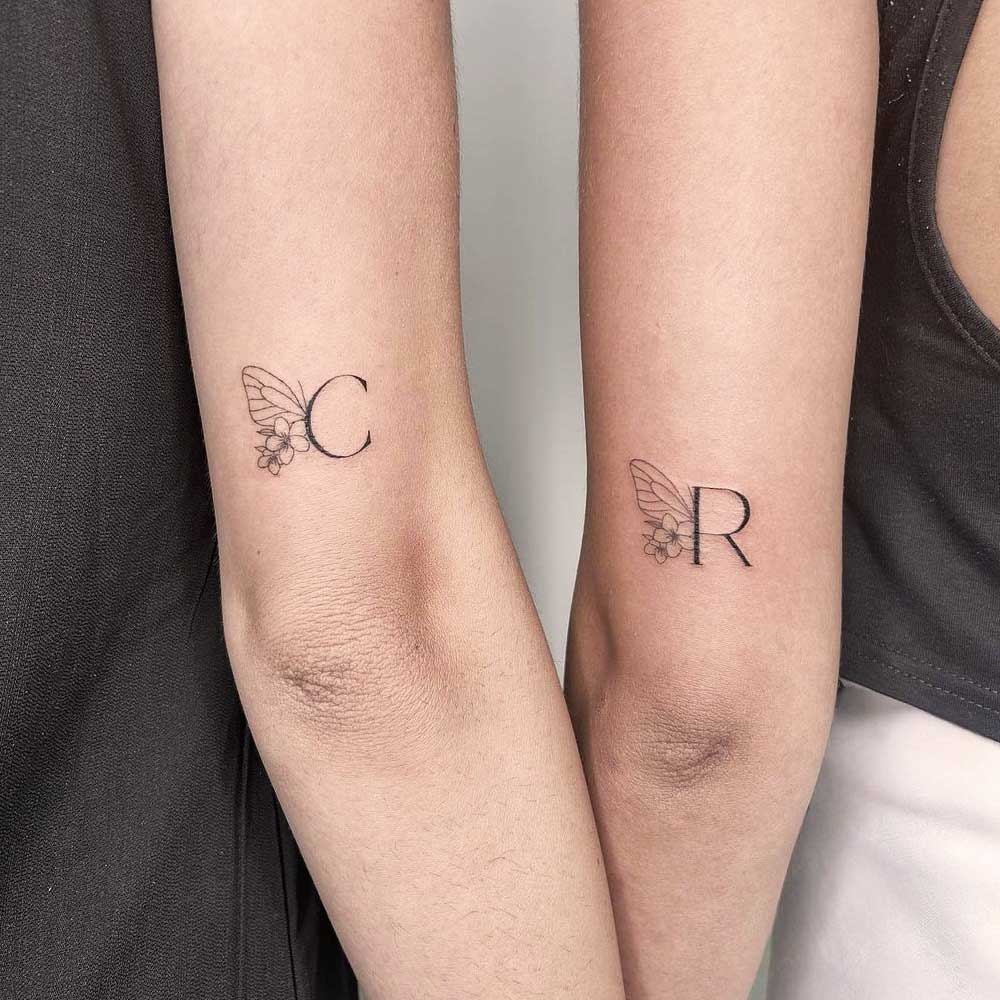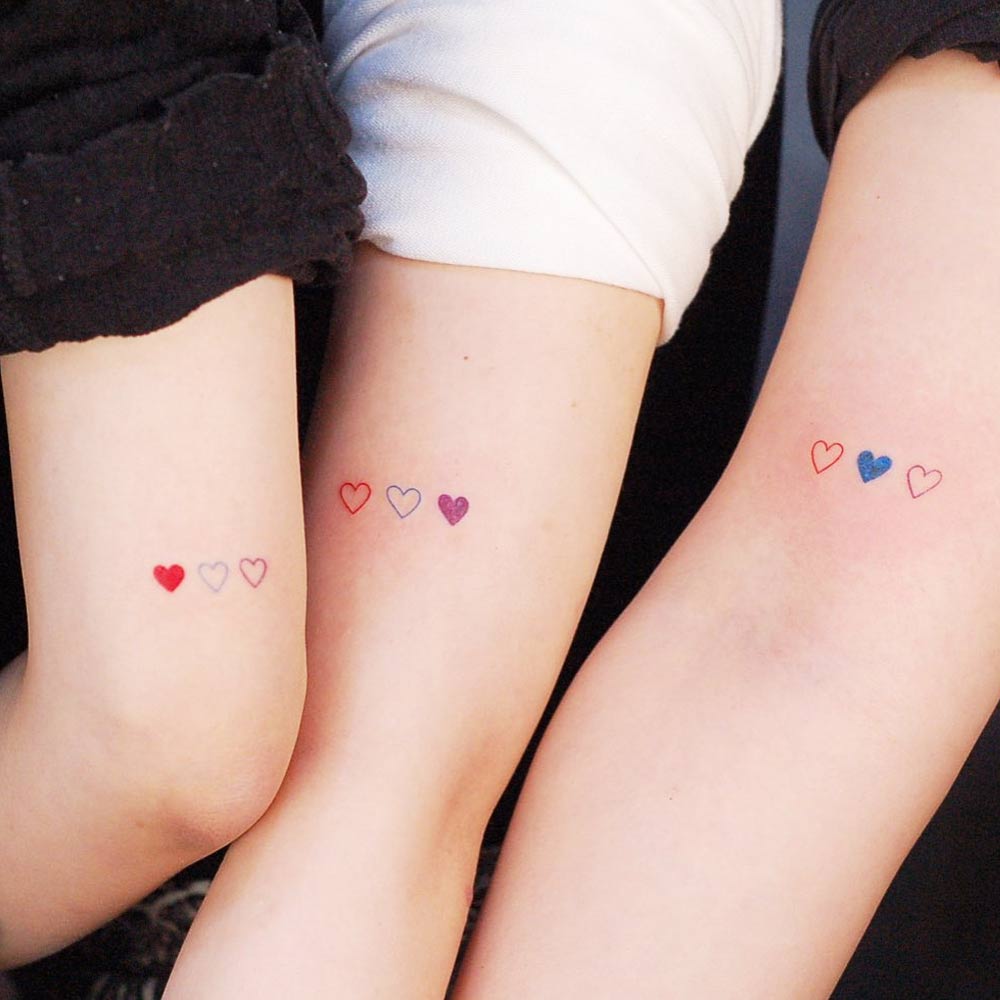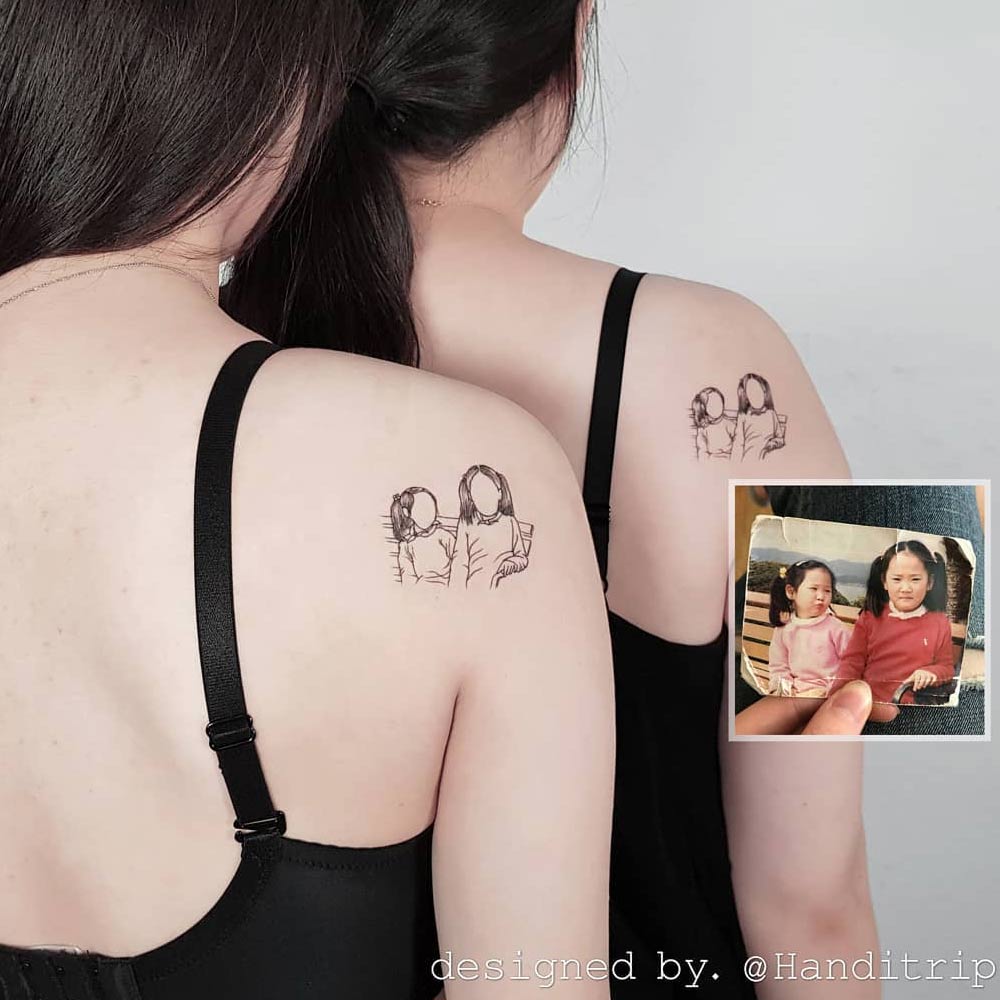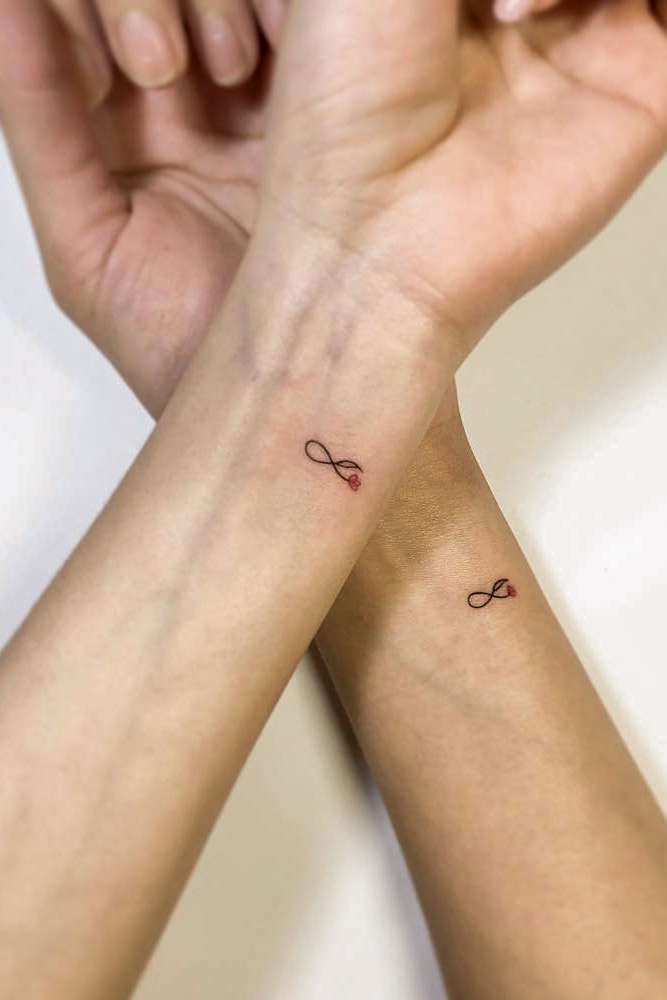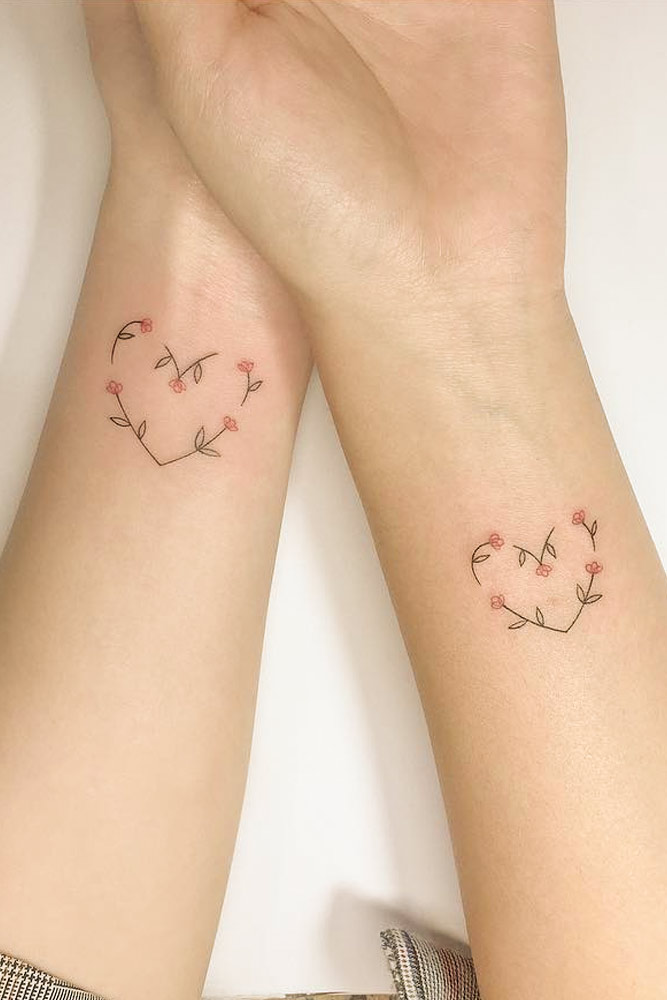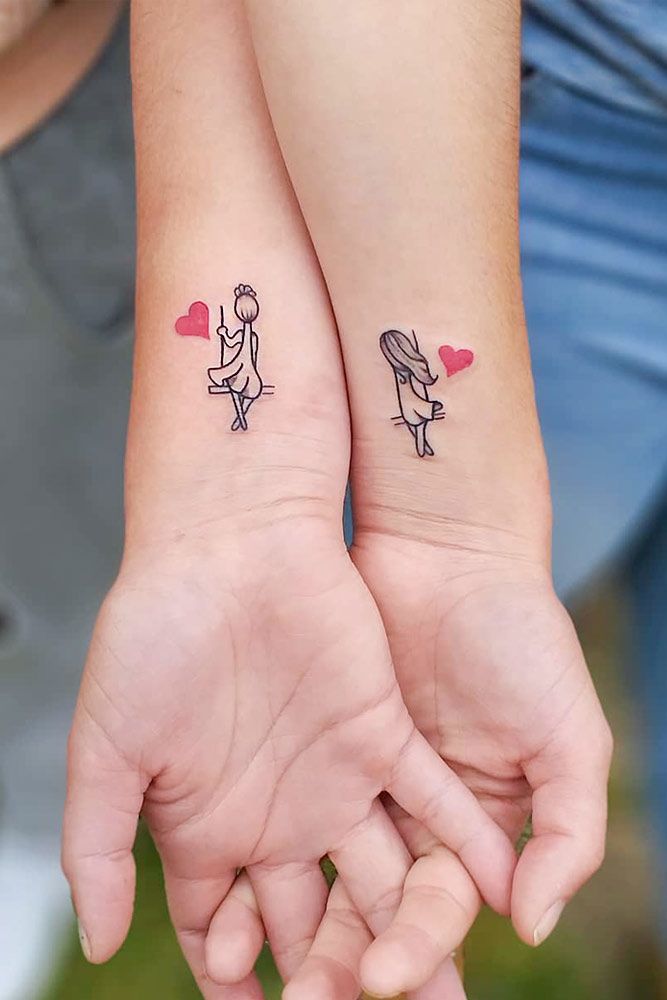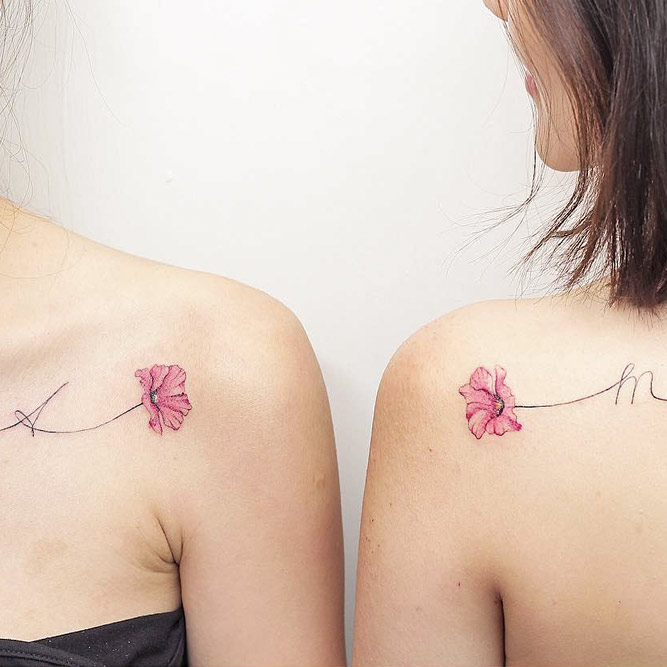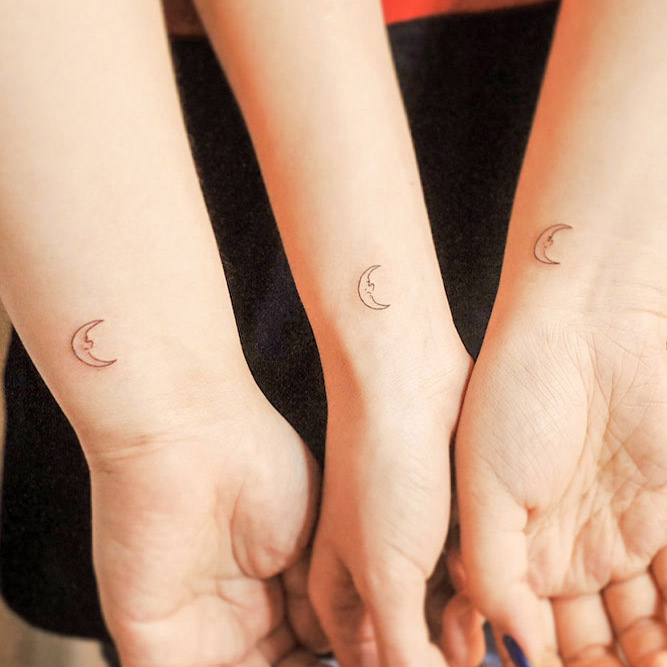These days the tattoo art is beyond popular, it seems that everyone in the world has something to say and everyone wishes to be able to understand it. That is why nowadays we can observe a new trend appearing – sister tattoos. There is rarely any other person in the world who will understand you better than a sister that is why committing each other to a matching tattoo art is that little thing you can do. Yet, when it comes to figuring out what you would like to have depicted on you – the difficulties may arise. That is why we think it is an excellent idea to share with you a handful of sister tattoo examples so that you can be inspired and come up with something of your very own.
*We may earn money from affiliate links on this page. Please check out our disclosure policy for more details.QUICK NAVIGATION
- ‘Love’ in Korean
- Side Body Flowers
- Matching Birth Flower Tattoos
- Butterflies and Initials
- Purrfect Match
- Colorful Hearts
- Floral Moons
Fingerprint Hearts
by @sp_polishFingerprint hearts reflect a unique story that unites you as your paths inevitably intertwine. Moreover, this design emphasizes your individuality and unconditional love for one another, no matter what. Additionally, such a tat looks like a perfect birthmark that all of you share, and that brings you even closer.
‘Love’ in Korean
by @naleak_tattooEven the most obvious phrase can be decoded so that only chosen ones can read it. A foreign language is a perfect option. If Korean isn’t your first language, you can choose it to reflect your love for another. However, pick a trustworthy translator who can approve the correctness of the wording.
Side Body Flowers
by @naleak_tattooMatching sister tats signify the unbreakable bond and connection between you. Floral designs are perfect for this purpose. You can conceptualize the idea by choosing those flowers that bear personal significance. Moreover, you can spice the ink up with meaningful quotes, dates, and other details.
Matching Birth Flower Tattoos
by @naleak_tattooEveryone has a birth flower, and you can use yours as a perfect source of inspiration to come up with matching sister tats. Surely, the flowers will differ, but the design will be united with matching location and the deep symbolism it bears. You can go as far as to introduce other tiny details that will make the ink as personal and individual as possible.
Crystal Symbols
by @tattooist_uziYou are a true gem for your siblings, and they mean the same to you. That is why entitling each of you with a separate gemstone and then etching them in your skin is a perfect tribute to your devotion and eternal bond.
Butterflies and Initials
by @lydinktattooSisterly love and the unbreakable bonds are impressively solid and beautiful. No matter the changes you go through, your sibling will be there for you. To commemorate those ties, a graceful butterfly tattoo, personalized with meaningful initials, is a worthy homage to your special person.
Purrfect Match
by @inkerbelletattoosCat tattoos are not only adorable but also highly meaningful. A couple of puffy and cute kitties could be an ideal representation of you and your dearest sister. You can go a little further and use your favorite pet as the primary source of inspiration for the design.
Colorful Hearts
by @wittybutton_tattooWe wouldn’t surprise you if we said that heart tattoos stand for love. However, instead of going for a classy heart design, you can play around with the idea and make it personal and fun. Let’s say there are three of you: tattoo a row of three hearts above the elbow. Make each outline of the heart in a different color. You can choose the shades that are particularly meaningful to you. Ask the tattoo artist to fill out only one heart per person, and make sure that the colors do not repeat so that you remain a loved and cherished individual just for who you are!
Floral Moons
by @handitripMoon tattoo is not only an ode to the mystery of the universe and its ethereal beauty. The celestial allure combined with gentle flowers results in a creative representation of sisterly love and dedication. To personalize your design, you can choose your favorite flowers and entitle each petal with a meaningful event and shared memories. Transform nature’s mystical element into a pure testament to sisterly love.
Childhood Portraits
by @handitripWhat can be more unique and personal than a childhood photo of two sisters? Pick an especially memorable picture and transform it into a highly symbolic and powerful sisterly ink. Sometimes, a sketch is worth more than a full-scale painting since it contains genuine emotions, feelings, and memories.
Small Shoulder Butterflies
by @handitripPeople like butterfly tattoos for various reasons. Usually, it is the metamorphosis that attracts those going through changes. However, the other meaning of the butterfly is no less powerful. This gorgeous little creature is exceptionally gorgeous and special. It is attracted to beauty and spreads the same aura around. Two amazing butterflies, side-by-side, will bring a lot of color to the grey reality. You and your dear sister are those rays of sunshine for one another and those around you!
Minimalistic Matching Moons
by @wittybutton_tattooPowerful feelings do not require pompous representations. A crescent moon outline contains deep connotations that only a few are entitled to. The simplicity and the enigma make the design twice as attractive.
Tree Tattoos
by @hansantattooNot everyone knows that a beautiful tree tattoo is more than an ode to nature’s beauty. It is also a tribute to the resilience and strength of sisterhood. You can pick different types of trees that reflect your sister’s personality best, or you can go for the same mighty trees to stand tall no matter what life throws at you.
Ankle Hearts with Flowers
by @nurburginkSimple tattoos serve as more of a reminder of something grand and meaningful that express it directly. A flower growing out of a heart can mean the beauty that grows out of your sisterly love. However, it can also project cheerful memories, shared tears, and laughter, yet only you will know those.
Eternal Sign
by @playground_tat2Matching sister tattoos are not only the way to appreciate the modern tattoo trends; getting matching tattoos, even though they may sometimes differ, at least in color – is the best way to celebrate your relationship with the loved sibling. Of course, the tattoo can be symbolical or can be a reminder of a particular event, but in most cases, it is all about the connection. Getting a sister tattoo is a beautiful way to show each other how much love and appreciation you have for each other. Don`t try to find crazy ideas, sometimes simple tattoos like this one are the best option.
Cute Matching Sisters
by @kity.recycleThis cute idea will make hearts melt when seen by other people, don`t you agree? A special idea that will only be full when you two are together.
Mandalas for Two
by @ifyrefiniA false opinion circles that sister friendship tattoos are supposed to view that deeper meaning that you depict in it. However, if you do not want to declare your feelings, wearing your heart literarily on the sleeve, a matching mandala pattern is a stylish way out. Think about it!
Minimalistic Branches
by @playground_tat2Very often those who opt for a sister tattoo are not always huge ink addicts that is why it is more than necessary to come up with something tiny but meaningful. It is true that small sister tattoos are many, but in most cases, they are something very special and particular for both. It may be your zodiac signs, your sister’s name, or it can be something very abstract that only the two of you may know the meaning of.
Heart Tattoos Designs
by @mini_tattooerIt should be mentioned that, whether you like it or not but flowers and hearts are the most requested for designs when it comes to sister tattoos.
by @playground_tat2Not only the love between a man and a woman can be expressed through the heart-shaped tattoo, but sister love also fits in just as well. A cute entwined heart tattoo is a perfect symbol to state your care and devotion.
by @la_tinta_de_allanLove is what we would love to show with having such tattoos, so why don`t we put a symbol of it near a tattoo that we address to our sibling?
Forearm Roses
by @darcy_lbIf you are looking for a creative and original idea for a sister tattoo, then think of adding a thin lined flower next to the word sister. So much tenderness and beauty.
Minimalistic Shoulder Flowers
by @mini_tattooerIt happens so that when you think about sister friendship tattoos, not only the design matters but also the placement. You need to think about it thoroughly where you are going to put your matching tattoo.
Lotus Flowers
by @cherryb.tattooWe say – the simpler, the better. The fact is that simple sister tattoos are usually the most meaningful ones. If you are looking for a trendy suggestion, then a lotus flower may be what you are searching for!
by @north88inkSometimes the phrase you depict on your skin matters more than the picture. Sister matching tattoos stating your feelings for one another are incredible! In case you do not trust us – see for yourself!
Cute Otters
by @cprtattoosIt is true that such sweet designs can represent many things that a sister tattoo is about. However, you need to keep it in mind that everything in this world has its special meaning, be it an animal or just a flower - you need to research the subject before getting it permanently inked on you and your fav sis. Who knows, maybe you will fall the victim of these tattoo ideas’ charm too!
Wrist Geometric Deer
by @rad.winederlustGeometry is trending at the moment, and we suggest you make use of it. Mix the strictness of geometry with your spirit animal, and the result you get will be breath-taking!
The Sun and Moon
by @neskatattooVery often, the union of the Sun and the Moon is viewed as something romantic and fit for couples in love only. We say that sisterly love deserves its share of attention, too, and inking these stellar elements on your bodies is a worthy idea.
Sister Tattoos For 3
by @playground_tat2So far we have been talking about double tattoos but what if you have two sisters instead of one? Of course, if there are three of you and all of you are equally close, then you should undoubtedly celebrate the bond with sister tattoos for 3. When it comes to a triple tattoo you need to take a lot of things into consideration since even though you are close and related you need to think about everyone’s lifestyle and preferences when coming up with the tattoo idea.
The world of tattoo art is gaining huge popularity these days, but apart from individual tattoos, people opt more and more often for something called sister tattoos. That is why if you have a sibling and you love her about all to the point of getting a tattoo together, we have got a ready compilation with some exciting ideas to get inspired with!
FAQ: Sister Tattoos
What is a symbol for sisterhood?
The Celtic Sisters Knot is a symbol of sisterhood and the unbreakable, eternal bond we share with our sisters and friends. Also called triquetra that looks like a triple spiral, that symbolizes the three stages of woman. First stage depicts the youth of our childhood. Second, the mothering spirit. Third, our wisdom that we pass on to the new generations.
Is there a symbol for siblings?
It is possible to use the Trinity knot as a symbol which represents the unity of your brother or sister.
Was this article helpful?